The blockchain facilitates decentralized networks and platforms that have no central authority. However, ungoverned blockchain platforms that use the permissionless blockchain access model can lead to unwanted users joining public blockchain platforms just to scam other users.
To prevent this, there exists a blockchain access model that uses a governing and hierarchical structure. In this model, users need permission to join the blockchain platform. This model is called the permissioned or private blockchain.
These models have their own use cases and are suitable in different contexts, even if permissionless blockchains seem like a security risk at first glance.
Permissionless blockchain platforms are very common and have more support from the open-source community, for example, Ethereum and Bitcoin. However, this model is not good for organizations and communities that want hierarchical privileged rights and strict access.
Therefore, it is imperative to know your decentralized application’s needs in order to match them with a suitable blockchain access model. In this guide, you will learn the infrastructure differences between permissioned and permissionless blockchains to determine which is best for your DApp.
Contents
- What is a permissioned blockchain?
- What is a permissionless blockchain?
- Which blockchain is best for your DApp?
- Conclusion
What is a permissioned blockchain?
The permissioned or private blockchain access model has administrators that regulate and prospect the blockchain platform regularly. It has a governing structure where different members have various roles and authority. Unlike permissionless blockchains, one needs access rights to access and use the permissioned blockchain.
Quorum and Corda are examples of permissioned blockchain. Quorum provides permissioned DeFi services to financial institutions and enterprises, while Corda is a blockchain project that enables individuals and companies to build interoperable blockchain networks that allow them to communicate and make direct transactions with other businesses.
Permissioned blockchains require identity and role definition called KYC (Know Your Customer) compliant before being given access rights. KYC compliance is a process that verifies the identity of the customer in order to prevent fraud and corruption.
Because anyone who wants to join a permissioned blockchain platform needs permission access, its network is fast because there will be very few users who have access. Also, the administrators can control the number of users who access the platform or specific features. Being able to adjust user traffic means that the blockchain will be easy to maintain.
It is easy to regulate a community built on permissioned blockchain as you can suspend malevolent members. It is also easy to track changes and delegate authority to high participating members.
Permissioned blockchains are not 100 percent transparent because the platform owners or administrators get to decide how much information to share on the blockchain platform. Ordinary members will not be able to detect any faults or track certain data.
To improve transparency and privacy, administrators can use permissioned and permissionless blockchains at the same time. When these two models are used at the same time, the combination results in a new blockchain model called a hybrid blockchain.
In a hybrid blockchain model, a certain portion of services, features, and processes is kept private while another part of the blockchain remains public.
What is a permissionless blockchain?
A permissionless blockchain does not have a central governing body. Members do not need permission access to join the permissionless blockchain platform or community. Unlike permissioned blockchain, users can remain anonymous when using a permissionless blockchain.
Ethereum and Bitcoin are some of the first permissionless blockchain platforms. These platforms are open source and use consensus algorithms to validate blocks and incentivize those who validate (or mine) them.
This model allows all users to view all transactions happening on the blockchain platform. For example, Etherscan, a platform that records and displays Ethereum transaction activities.
Because a permissionless blockchain does not have a governing body or owner, this model uses a consensus algorithm to facilitate all transactions and activities that occur on the platform.
Permissionless blockchains use different consensus algorithms such as:
- Proof of Work (POW)
- Proof of Stake (POS)
- Effective Proof of Stake (ePOS)
These consensus algorithms determine how miners who validate blocks are given tokens as compensation. These consensus models promote security, because miners validate blocks and can revoke any malicious blocks. Ironically, this makes permissionless blockchain safer and more secure than permissioned blockchain.
Although permissionless blockchains seem insecure, corrupting data is hard in this model because more than 50 percent of the participants would have to agree to corrupt data.
Which blockchain is best for your DApp?
This section is intended to show you which infrastructure is the best for your DApp by looking at different use cases and characteristics of permissioned and permissionless blockchains.
The following are some of the factors you should consider when deciding which blockchain access model is right for you.
Censorship and transparency
If your DApp’s main priority is to promote privacy and transparency, then a permissionless blockchain is the best for your application. Permissionless blockchains are also the best when it comes to maintaining privacy and transparency, because users can be anonymous and all transactions can be seen by everyone. All users are equal and have equal access. No administrators can censor the DApp’s users.
Permissioned blockchains are not the best in this case because there is one person with rights who can corrupt data. It is also hard to maintain a consensus algorithm if those in control are going to alter it for their own benefit.
Commercialization
Permissioned blockchain has been doing well in the NFT market space. When a user buys an NFT they gain entry to a permissioned blockchain. This entry gives them more perks such as yachting with other members. This access is only restricted to blockchain members who have not bought the NFT.
The best part about permissioned blockchain is that it is well regulated and is good for business, because the business gets to choose who has access to their private blockchain.
Performance and security
Permissioned blockchains are faster when compared to permissionless blockchains because they manage the number of users who can access and join the permissioned blockchain.
Permissioned blockchain, however, does not have effective security when compared to permissionless blockchain because there are no or few validators who validate the blocks or activities. Every block or transaction happening in a permissionless blockchain has to be validated before being added.
A permissionless blockchain is easy to maintain because there are millions of members reporting bugs and validating blocks. Administrators in a permissioned blockchain can carry out security measures, but they are not as effective as in the permissionless blockchain.
Community contribution and ecosystems
FAANG companies and Ethereum Layer 2 platforms are successful because their source code is open source. Open sourcing your decentralized application’s source code is beneficial because you will be receiving reviews, updates, and ideas from developers from around the world.
DApps that are open sourced experience fast development and technology evolution. A permissionless blockchain is best for this use case because it is good for voting and fundraising programs. This is because everyone is allowed to join the fundraising program and contribute to the source code.
Permissionless blockchain also provides a way for contributors to be compensated with cryptocurrencies. The compensation process is facilitated by consensus algorithms.
Power usage
A study carried out by MoneySuperMarket has revealed that a single Bitcoin transaction uses at least 1,173kWh. This energy is enough to power a house for more than a month. All of these cryptocurrencies that mine tokens use the permissionless blockchain. This is because there are many transactions being carried out that need to be validated by crypto miners.
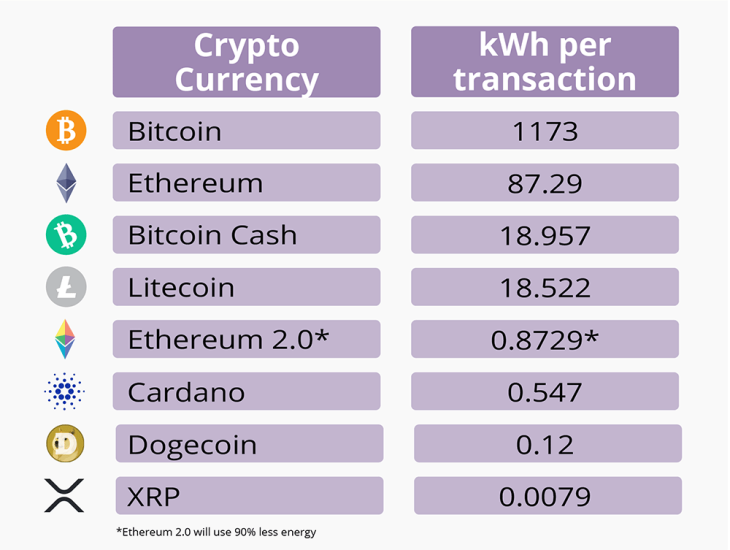
The permissionless model uses a lot of energy when mining and validating blocks. It is also difficult to scale your DApp when using the permissionless blockchain because there are many unknown users joining every day and carrying out transactions.
A permissionless blockchain is expensive because validators have to be incentivized. Many permissionless blockchains such as Ethereum and Harmony have created their own cryptocurrencies and tokens they use to incentivize their validators. This is an effective strategy, but getting a crypto coin to have real value that can be traded in the public market is not easy. The value of the cryptocurrency will be tied to the performance of the blockchain platform. There is also a lot of competition in this space.
Web customization and flexibility
Permissioned blockchain DApps are easy to customize and satisfy their audience because they have a small audience and user base, plus administrators and owners who dedicate their time to designing the platform’s specific needs. This process is fast because there is no voting process needed to choose which updates are pushed to the DApp’s codebase.
Conclusion
The hybrid model lies in between the permissioned and permissionless blockchain. This model is the best for many DApps as it does not restrict you to choosing only one blockchain access model and allows your users to switch from permissioned features to permissionless features.
In a nutshell, permissionless blockchains are good for public platforms and apps; all users are equal, and no one is above the blockchain consensus. Permissioned blockchains, however, are good for DApp’s that have strict data access.
But the best blockchain access model is the one that meets your DApps needs. Hopefully, you can use the criteria I have laid out in this article to make an informed decision for your next project.
The post Permissioned vs. permissionless blockchains for DApps appeared first on LogRocket Blog.
from LogRocket Blog https://ift.tt/2LBSZuV
via Read more



